Web5 in 5
"Web5 Unleashed: A User-centric revolution where privacy leads and data is given back to its owners😊🚀✨
The untimely death of the talented Nigerian afrobeat artist, Mohbad, sent shockwaves across the nation, sparking a movement for justice and accountability. The tragedy highlighted the critical need for innovative solutions in the healthcare sector, prompting us to explore the potential impact of technologies like Web5 on preventing such incidents.
The Tragedy Unveiled:
Mohbad's demise, attributed to a nurse's unwitting administration of incorrect medication, sheds light on the gaps in our current healthcare system. The issue wasn't a lack of intention on the nurse's part but rather a lack of immediate access to Mohbad's health records. This tragedy underscores the urgency for a system that can provide instant and secure access to critical health information.
Web5: Bridging the Gap in Healthcare:
Imagine a world where every individual holds a Decentralized Identifier (DID) connected to their Decentralized Web Node (DWN). In emergencies, users can securely share their health records, empowering medical professionals with vital information. In Mohbad's case, swift access to his health history could have altered the outcome. Web5, with its promises of decentralized technologies, stands as a potential solution to save lives in critical situations.
The Ripple Effect: Beyond Healthcare:
The repercussions of Mohbad's tragedy extend beyond healthcare. The administering nurse, acting with good intentions, now faces legal consequences. This incident highlights the profound impact of data-related events and emphasizes the need for a more secure and user-centric approach.
Web5's Core Tenets and Differentiators:
At the heart of Web5's philosophy are three pillars: self-owned decentralized identifiers, verifiable credentials, and decentralized web nodes for storing data and relaying messages. These pillars align with the core tenets of Web3's decentralized identity systems, emphasizing user control and data ownership.
Web5's approach distinguishes itself by working with existing Web2 services rather than seeking to replace them entirely. This integration allows for interoperability, enabling services like Groove to add playlists to a Web5 user's decentralized identifier. The decentralized identifier ensures that users can seamlessly transfer their preferences across different platforms.
Addressing Web3 Challenges and Jack Dorsey's Vision:
Web5's founder, Jack Dorsey, brings a unique perspective by aligning with Bitcoin and distancing the platform from Web3 culture. Web5 operates without special utility tokens or subjective consensus, emphasizing the need to rid Web3 of centralized actors. This approach resonates with Dorsey's vision of keeping the taste of Web3 without the associated complexities.
Cryptographic Foundations and the Wider Web Consortium Standards:
Web5, in its commitment to user-controlled data and identity, aligns with the cryptographic principles underpinning decentralized technologies. Moreover, it provides a framework to apply the new identity standards set by the World Wide Web Consortium (W3C). These standards aim to enhance user privacy, security, and control over their digital identities. visit w3c to read more
Challenges and the Road Ahead:
While Web5 holds immense promise, challenges lie ahead, including concerns about trademarking and the platform's revenue model. The backing of Jack Dorsey provides a strong foundation, but the platform's long-term success will depend on widespread adoption and overcoming ideological and practical hurdles.
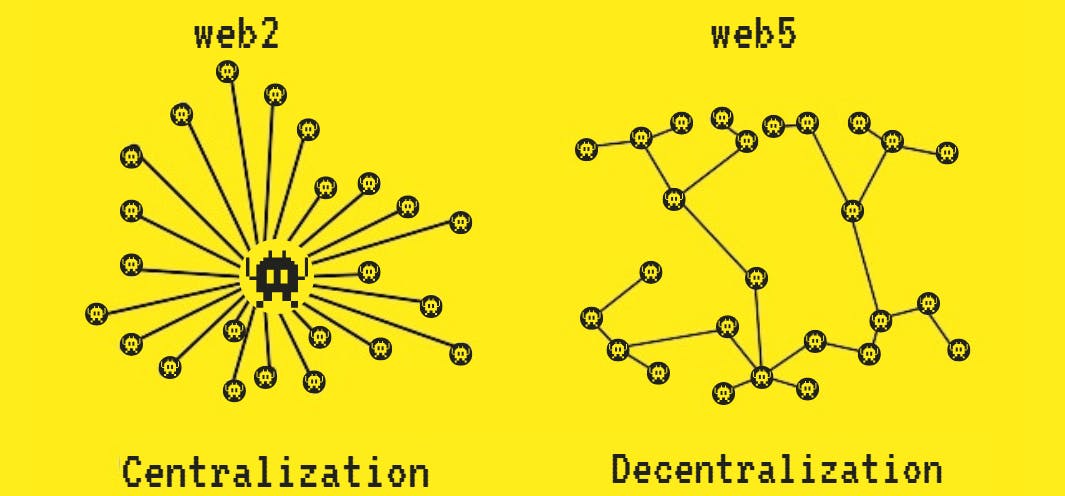
The Vulnerability of Centralized Systems:
Centralized systems pose significant risks, from unauthorized access to potential exploitation. The power and wealth entrusted to industry giants come with inherent vulnerabilities. The famous Endsars movement in Nigeria, where government authorities exploited centralized financial data, showcases the dangers of such systems. Well-meaning citizens had their accounts blocked and were placed on a no-fly list simply because they had unrestricted access to all their data. Additionally, centralized storage of health records raises concerns about data falling into malicious hands.
Web5: A Paradigm Shift in Digital Landscape:
The intersection of technology and healthcare, exemplified by Web5, not only revolutionizes emergency medical care but addresses the legal aftermath of well-intentioned actions. It signifies a shift from centralized control to user-centric empowerment, offering solutions to data security and privacy concerns.
Understanding Web5:
Web5, an open-source project by TBD (to be decentralized), takes a unique approach, bypassing the complexities of Web3 and embracing a user-centric model powered by JavaScript. Its integration of AI on the Web5 API adds advanced capabilities while maintaining accessibility. With the potential for AI integration, Web5 becomes a versatile and evolving platform
Decentralized Identifiers (DID) and Decentralized Web Nodes (DWN):
Web5's technical prowess lies in Decentralized Identifiers (DID) and Decentralized Web Nodes (DWN). DID serves as a unique digital fingerprint, ensuring users have control over their identity. Selective sharing allows users to dictate who gains access to their identity, crucial in areas like health records. DWNs form the backbone of Web5's decentralized architecture, distributed across the network to create a resilient and tamper-resistant infrastructure. Installing the web5 API is as simple. You can run the code below to get started
npm install @web5/api
According to W3c
A DID is a simple text string consisting of three parts: 1) the did URI scheme identifier, 2) the identifier for the DID method, and 3) the DID method-specific identifier.
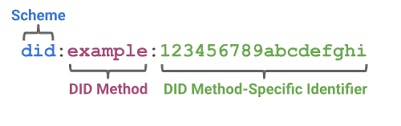
The example DID above resolves to a DID document. A DID document contains information associated with the DID, such as ways to cryptographically authenticate a DID controller.
{
"@context": [
"https://www.w3.org/ns/did/v1",
"https://w3id.org/security/suites/ed25519-2020/v1"
]
"id": "did:example:123456789abcdefghi",
"authentication": [{
"id": "did:example:123456789abcdefghi#keys-1",
"type": "Ed25519VerificationKey2020",
"controller": "did:example:123456789abcdefghi",
"publicKeyMultibase": "zH3C2AVvLMv6gmMNam3uVAjZpfkcJCwDwnZn6z3wXmqPV"
}]
}
Web5 Advantages:
- User-Controlled Data Deletion: Web5 ensures that when users delete data from their DWN, it's permanently erased, minimizing privacy risks.
- Enhanced Cybersecurity: Unlike centralized servers, Web5's decentralized architecture significantly reduces vulnerabilities, enhancing overall cybersecurity.
- Immutable User Autonomy: Web5 empowers users to dictate the fate of their content without external interference, a stark contrast to traditional platforms.
- End-to-end Encryption: Privacy is reinforced through end-to-end encryption, ensuring data remains secure from sender to recipient.
- Data Sovereignty Assurance: Web5 guarantees data sovereignty, keeping user information within their chosen legal jurisdiction.
Web5 vs. Web3: A Practical Edge:
Web5's streamlined approach presents practical advantages over the complex blockchain methodologies of Web3. Unlike Web3's reliance on blockchain, Web5 harnesses decentralized nodes without the need for intricate and energy-consuming blockchain infrastructure. This makes Web5 more accessible and user-friendly, offering seamless integration into existing Web2 technologies. This may involve;
1. Seamless Transition from Web2 to Web5: Developers can integrate Web5 functionalities into existing Web2 technologies, minimizing the learning curve associated with blockchain API. Visit TBD documentation for a quick start
2. Avoiding Cryptocurrency Quandaries: Web5 sidesteps the need for end-users to handle cryptocurrencies, offering decentralized functionality without payment complexities.
3. Navigating Legal Restrictions: Web5 emerges as a feasible alternative in regions with cryptocurrency regulations, aligning with government policies and avoiding potential legal issues tied to blockchain.
4. Empowering Developers and Users: Web5 empowers developers to deliver innovative, user-centric applications without delving into the complexities of blockchain technology.
Why It Matters:
Beyond privacy concerns, the potential misuse and exploitation of personal data impact trust in financial institutions. Web5 prioritizes user privacy and data integrity, positioning itself as a trustworthy alternative.
Conclusion:
Web5's commitment to privacy, user empowerment, and cybersecurity resilience makes it a promising alternative to the complexities of Web3. By addressing critical issues in healthcare, legal consequences, and the vulnerability of centralized systems, Web5 emerges as a transformative force in the digital landscape. The enhanced control over data, cybersecurity measures, user autonomy, and transparent governance underscore Web5's innovative and user-friendly approach. As we navigate the evolving technological landscape, Web5 stands as a beacon of change, redefining the digital equation and paving the way for a decentralized future. To know more, visit tbd official website or join the discord community. To contribute to the open-source project, visit the GitHub repository
